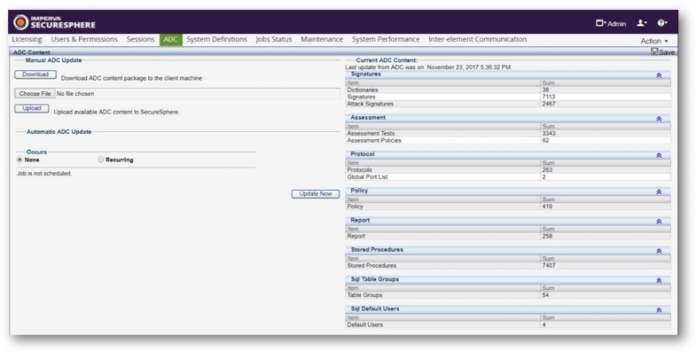
Configuring Imperva SecureSphere for GDPR Compliance: Part One
Time is running out. 23 days until GDPR enforcement
The GDPR effective date is less than a month away and, given the significant risk and potential costs associated with a failure to comply, organizational readiness efforts continue to mount. GDPR non-compliance penalties can be severe (up to 79 times higher than existing guidelines), and GDPR applies to any organization of...
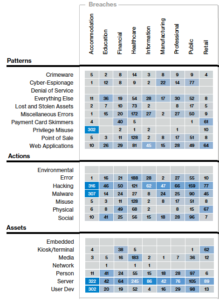
Insights from the Verizon 2018 Data Breach Investigation Report
The 2018 Verizon Data Breach Investigation Report (DBIR) was published in early April, reporting on 53,308 security incidents and 2,216 data breaches from 67 contributors in 65 countries.
It’s an important read for organizational leaders, and cyber professionals to find data-driven evidence of industry-specific incident patterns. It’s also important to distinguish incidents from breaches. A breach is an incident that...
Securing the Entire Container Stack, Lifecycle and Pipeline
Securing the Entire Container Stack, Lifecycle and Pipeline #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
DevSecOps Gathers More of the Spotlight at RSA 2018
Nearly 1,200 security professionals recently attended the DevOps Connect: DevSecOps Day at the 2018 RSA Conference at San Francisco’s Moscone Center.
Now in its fourth year, DevSecOps Day featured presentations and panel discussions on the role of security in the world of DevOps. DevOps thought leaders, security experts, and vendors shared success stories, insights, and challenges they faced in their...
The Catch 22 of Base64: Attacker Dilemma from a Defender Point of View
Web application threats come in different shapes and sizes. These threats mostly stem from web application vulnerabilities, published daily by the vendors themselves or by third-party researchers, followed by vigilant attackers exploiting them.
To cover their tracks and increase their attack success rate, hackers often obfuscate attacks using different techniques. Obfuscation of web application attacks can be extremely complicated, involving...
Drupalgeddon3: Third Critical Flaw Discovered
For the third time in the last 30 days, Drupal site owners are forced to patch their installations. As the Drupal team noted a few days ago, new versions of the Drupal CMS were released, to patch one more critical RCE vulnerability affecting Drupal 7 and 8 core.
The vulnerability, code-named Drupalgeddon3, exploits improper input validation in the Form API....
FS-ISAC 2018 Summit
<img src="https://info.digitalguardian.com/rs/768-OQW-145/images/fsi-isac-logo.png">
Digital Guardian will be presenting and exhibiting in Booth #69.Get tools, tips and recipes from our threat hunting experts.
Boca Raton | May 20-23 | Boca Raton Resort
- Read more





![[Case Study] Delivering Security Needs On Time](https://www.dataproof.co.za/wp-content/uploads/2018/04/case-study-delivering-security-needs-on-time.jpg)





