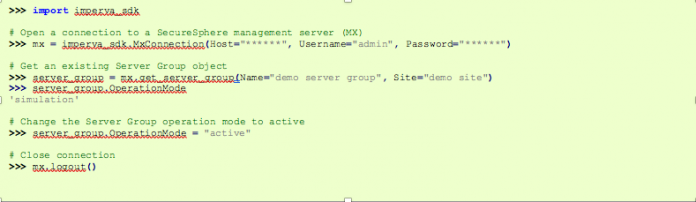
Imperva Python SDK – We’re All Consenting SecOps Here
Managing your WAF can be a complicated task. Custom policies, signatures, application profiles, gateway plugins… there’s a good reason ours is considered the best in the world.
Back when security teams were in charge of just a handful of WAF stacks and a few dozen applications, things were relatively manageable. Today, however, with the shift to cloud and microservices, organizations...
OPC UA security analysis
This paper discusses our project that involved searching for vulnerabilities in implementations of the OPC UA protocol. In publishing this material, we hope to draw the attention of vendors that develop software for industrial automation systems and the industrial internet of things to problems associated with using such widely available technologies, which turned out to be quite common. We...
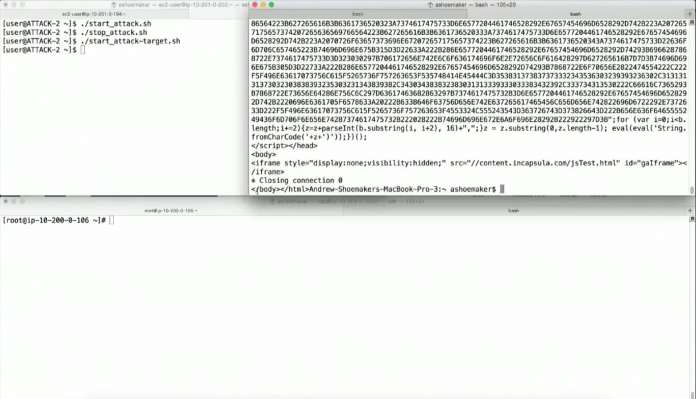
Want to See What A Live DDoS Attack Looks Like?
We’re fortunate enough to have had Andy Shoemaker, founder of NimbusDDoS, and our own Ofer Gayer chat about DDoS attacks and shed some light on the gaps in many people’s understanding of the threats out there.
In a new BrightTALK webinar alongside Imperva Senior Product Manager, Ofer, Andy discusses the trade-offs of manual versus automatic mitigation strategies, and to that effect showed...
Jumpstarting Your Cyberdefense Machine with CIS Controls V7
Jumpstarting Your Cyberdefense Machine with CIS Controls V7 #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important;...
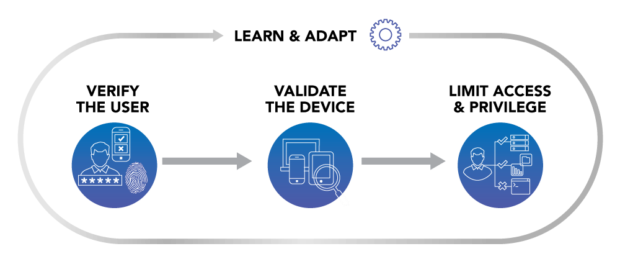
How to Operationalize the Zero Trust Security Pillar ‘Limit Access & Privilege’ with ServiceNow
An easy way for a cyber-attacker to gain access to sensitive data is by compromising an end user’s identity and credentials. Things get even worse if a stolen identity belongs to a privileged user, who has even broader access, and therefore provides the intruder with “the keys to the kingdom.”
As a result, it’s not surprising that, according to Forrester,...
Gartner Security & Risk Management Summit 2018
Gartner Security & Risk Management Summit 2018
June 4th – 7th | National Harbor, MD
- Read more
SynAck targeted ransomware uses the Doppelgänging technique
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this sophisticated technique in an attempt to bypass modern security solutions.
In April 2018, we spotted the first ransomware employing this bypass technique – SynAck ransomware. It should be noted that SynAck is not new – it...
World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my life, if Outlook or Android doesn’t serve me a popup reminder, I’m oblivious to it.
But this one commanded my attention, not only because of the never-ending news coverage we see about high-profile breaches, but also...
Who’s who in the Zoo
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation infect Android devices using several generations of malware, with the attackers including new features in each iteration. We label them from v1-v4, with v4 being the most recent version deployed in 2017. From the technical...