Threat Prevention is Foundational
Threat Prevention is Foundational #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff; }...
Centrify Does it Again – Innovative Security Analytics Integration with Palo Alto Networks App Framework
Centrify and Palo Alto Networks have announced another important integration that can help customers quickly and decisively discover anomalies that are a security threat.
Building on our past partnership, both companies collaborated anew around the Centrify Analytics Service and the Palo Alto Networks App Framework to more-readily share threat intelligence. When security stalwarts like Centrify and Palo Alto Networks combine...
Facebook, GDPR and the Right to Privacy: Three’s a Crowd?
Back in 2016 the European Union voted to pass the mother of all security laws, aimed at further extending the rights of its citizens to control how their data is used. The General Data Protection Regulation (GDPR) guards users against having their information shared without their explicit consent, and gives them the right to revoke that consent at any...
Roaming Mantis dabbles in mining and phishing multilingually
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which is designed to spread via DNS hijacking and targets Android devices. This activity is located mostly in Asia (South Korea, Bangladesh and Japan) based on our telemetry data. Potential victims were redirected by DNS hijacking...
Analyst Insights – Building An Efficient Data Security Program with Forrester
Analyst Insights – Building An Efficient Data Security Program
This webinar was recorded on May 17, 2018.
- Read more
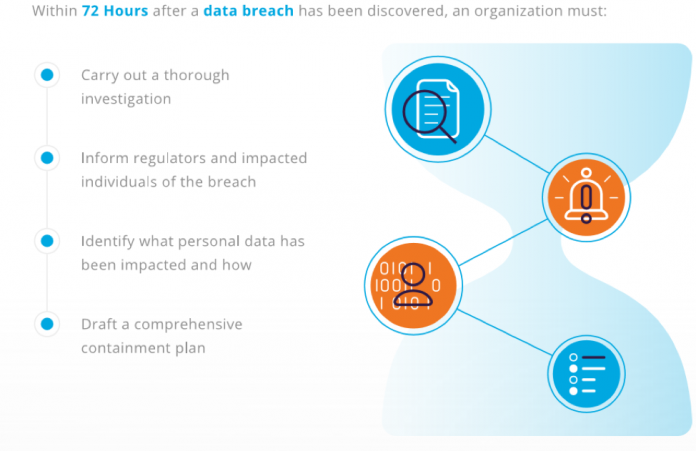
72 Hours: Understanding the GDPR Data Breach Reporting Timeline
We’re down to the wire with respect to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018.
Organizations that fail to comply could face fines of up to €20M (roughly $22M) or 4 percent of their annual global turnover from the prior year and we’ll soon see just how EU regulators will enforce the GDPR regulations.
One of...
Electronic Health Record Systems Under Attack
Electronic Health Record Systems Under Attack #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
Centrify and SailPoint Join Forces to Apply Zero Trust Security Best Practices to Identity Governance
Today, Centrify is proud to announce the integration of the Centrify Privileged Access Service with SailPoint® Technologies IdentityIQ solution.
This integration provides joint customers with a single pane of glass for a privileged user’s entitlements and enables issuing access requests for accounts, systems, and existing roles that are controlled by the Centrify Privileged Access Service. This allows for centralized management...
IT threat evolution Q1 2018. Statistics
Q1 figures
According to KSN:
Kaspersky Lab solutions blocked 796,806,112 attacks launched from online resources located in 194 countries across the globe.
282,807,433 unique URLs were recognized as malicious by Web Anti-Virus components.
Attempted infections by malware designed to steal money via online access to bank accounts were logged on the computers of 204,448 users.
Ransomware attacks were registered on the computers of...





![[VitalQIP Migration Series] Part 1: Three Reasons Why VitalQIP Migration Should Be on Your Radar](https://www.dataproof.co.za/wp-content/uploads/2018/05/vitalqip-migration-series-part-1-three-reasons-why-vitalqip-migration-should-be-on-your-radar.jpg)







