Clustering App Attacks with Machine Learning Part 1: A Walk Outside the Lab
A lot of research has been done on clustering attacks of different types using machine learning algorithms with high rates of success. Much of it from the comfort of a research lab, with specific datasets and no performance limitations.
At Imperva, our research is done for the benefit of real customers, solving real problems. Data sets can vary and performance...
SecurIT: Making Zero Trust a Reality for CIOs and CISOs
On June 13, C-level and senior management leaders from global companies spanning multiple industries will gather in San Francisco at SecurIT: the Zero Trust Summit for CIOs and CISOs.
Hosted by IDG (publishers of CIO and CSO) and Centrify, this first-of-its-kind event will provide greater understanding around the concept of Zero Trust Security. Specifically, it will help define what Zero...
Defending Critical Infrastructure against Cyber Attacks
Defending Critical Infrastructure against Cyber Attacks #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
Zero to Account Takeover: How I ‘Impersonated’ Someone Else Using Auth0
There’s a fine line between an unintended use and a bug; this was my conclusion after taking a look at Auth0, an identity-as-a-service offering with 2000 enterprise customers – more or less the size of Schneider Electric, Atlassian, Dow Jones, Nvidia, and Mozilla, among others – and 42 million logins a day.
In this post I’ll explain how this “unintended...
FIFA public Wi-Fi guide: which host cities have the most secure networks?
We all know how easy it is for users to connect to open Wi-Fi networks in public places. Well, it is equally straightforward for criminals to position themselves near poorly protected access points – where they can intercept network traffic and compromise user data.
A lack of essential traffic encryption for Wi-Fi networks where official and global activities are taking...
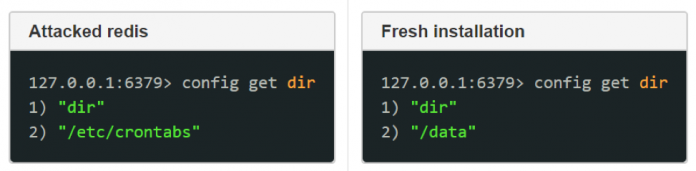
New research shows 75% of ‘open’ Redis servers infected
Since our initial report on the RedisWannaMine attack that propagates through open Redis and Windows servers, we’ve been hearing about more and more attacks on Redis servers.
Redis is a great tool, it can serve as in-memory distributed database, cache or a message broker and is widely popular. Redis is aimed at high performance and in doing so, some other...
Netkids
Children today are completely at home in the digital space. They use digital diaries and textbooks at school, communicate via instant messaging, play games on mobile devices (not to mention PCs and consoles), and create mini masterpieces on tablets and laptops. This total immersion in the digital universe is a concern for many parents, but if they want their...