Centrify Launches Zero Trust Security Network Ecosystem
The world has changed. I’m not sure if it was the HBO breach, Equifax, Yahoo, or one of the many breaches since, but after one of those we at Centrify realized it was one breach too many.
As we looked at how the breaches were increasing in number, size, and severity we knew we had to do something different. How...
LuckyMouse hits national data center to organize country-level waterholing campaign
What happened?
In March 2018 we detected an ongoing campaign targeting a national data center in the Central Asia that we believe has been active since autumn 2017. The choice of target made this campaign especially significant – it meant the attackers gained access to a wide range of government resources at one fell swoop. We believe this access was...
Clustering App Attacks with Machine Learning (Part 2): Calculating Distance
In our previous post in this series we discussed our motivation to cluster attacks on apps, the data we used and how we enriched it by extracting more meaningful features out of the raw data. We talked about the many features that can be extracted from IP and URL. In this blog post we’ll discuss one of the more...
DevOps Buyer’s Guide
DevOps Buyer's Guide #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff; } h1,.h1{...
Five Reasons to Kill Off the Password
Australia recognised the security problem posed by passwords through widespread media coverage of Centrify’s warning issued on World Password Day, which occurred on May 3 this year.
Centrify celebrated World Password Day, which turns up annually on the first Thursday of May as a day to promote good security hygiene and password habits, by calling for the end of this...
451 Research: Centrify Goes “All In” on the Zero Trust Movement
451 Research recently published an impact report recognizing Centrify as one of the early vendors to embrace the Zero Trust concept, which is a new conceptual framework on the rise as traditional security models that follow a hardened perimeter approach have failed.
The author, 451 analyst Garrett Bekker, notes these failures and states that “the very concept of trust is...
A MitM extension for Chrome
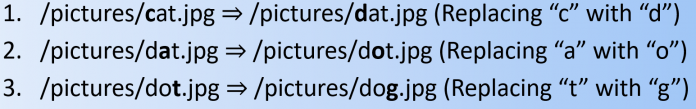
Browser extensions make our lives easier: they hide obtrusive advertising, translate text, help us choose in online stores, etc. There are also less desirable extensions, including those that bombard us with advertising or collect information about our activities. These pale into insignificance, however, when compared to extensions whose main aim is to steal money. To protect our customers, we...








![FW: [Demo] Detect Threats and Identify Unauthorized Changes](https://www.dataproof.co.za/wp-content/uploads/2018/06/fw-demo-detect-threats-and-identify-unauthorized-changes.jpg)





