Trending Now
Featured news
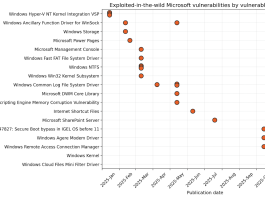
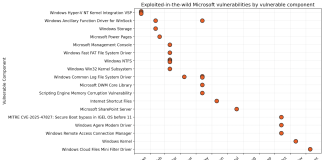
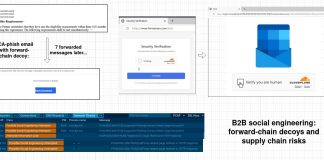
ShadowSilk Data Exfiltration Attack
FortiGuard Labs’ network telemetry has observed active exploitation of known vulnerabilities in Drupal Core and the WP-Automatic WordPress plugin for initial access. Following compromise,...
Tech News
Tech
Gartner Names PAM a Top Security Project (AGAIN!) in 2019
Last June at the 2018 Gartner Security & Risk Management Summit, the analyst firm issued a “Smarter with Gartner” paper outlining the Top 10...
Security
eBook: Driving DevOps Security
eBook: Driving DevOps Security #outlook a{ padding:0; } body{ width:100% !important; }...
Most popular
How Imperva’s New Attack Crowdsourcing Secures Your Business’s Applications
Attacks on applications can be divided into two types: targeted attacks and “spray and pray” attacks. Targeted attacks require planning and usually include a...
Moving Beyond Legacy PAM: Centrify Zero Trust Privilege
Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of...
Inside GoBruteforcer: AI-Generated Server Defaults, Weak Passwords, and Crypto-Focused Campaigns
Key takeaways
GoBruteforcer (also called GoBrut) is a modular botnet, written in Go, that brute-forces user passwords for services such as FTP, MySQL, PostgreSQL,...