Trending Now
Featured news
Driving DevOps Security: Scalable Best Practices
Driving DevOps Security: Scalable Best Practices #outlook a{ padding:0; } body{ width:100%...
Tech News
Tech
Centrify Closes Out a Busy June at AWS Re:Inforce and Identiverse
June has been a busy month in the cybersecurity space! It started off with InfoSec Europe and SailPoint Navigate, next week we’ll wrap up...
Security
Drupalgeddon3: Third Critical Flaw Discovered
For the third time in the last 30 days, Drupal site owners are forced to patch their installations. As the Drupal team noted a...
Most popular
Google Cloud Platform (GCP) Google Security Operations IDE Code Execution Protection Bypass
Google Cloud Platform (GCP) Google Security Operations IDE Code Execution Protection Bypass Tenable Research has identified and responsibly disclosed a safety mechanism bypass vulnerability...
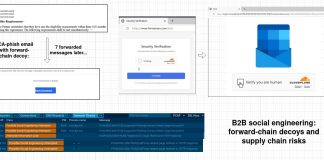
From Email to Exfiltration: How Threat Actors Steal ADP Login and Personal Data
By: Jhon Astronomo, Cofense Phishing Defense CenterRecently, threat actors have been impersonating employees at major companies, such as ADP, a leading global provider of...
Sicarii Ransomware: Truth vs Myth
Key findings
Sicarii is a newly observed RaaS operation that surfaced in late 2025 and has only published 1 claimed victim. The group explicitly brands itself...
A mining multitool
Recently, an interesting miner implementation appeared on Kaspersky Lab’s radar. The malware, which we dubbed PowerGhost, is capable of stealthily establishing itself in a...







![FW: [Case Study] Automated Change Management](https://www.dataproof.co.za/wp-content/uploads/2019/08/fw-case-study-automated-change-management-100x59.png)