|
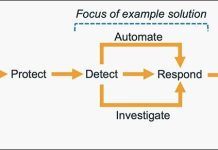
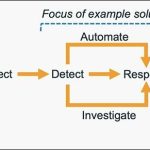
What is the Vulnerability? |
A Local File Inclusion (LFI) vulnerability (CVE-2025-68645) exists in the Zimbra Collaboration Suite (ZCS) Webmail Classic UI due to improper handling of user-supplied request parameters in the RestFilter servlet. An unauthenticated remote attacker can craft malicious requests, potentially exposing sensitive configuration and application data and aiding further compromise. Successful exploitation may allow threat actors to: |
|
What is the recommended Mitigation? |
• Apply vendor patches immediately for all affected ZCS versions (Zimbra Collaboration (ZCS) 10.0 – 10.0.17- Zimbra Collaboration (ZCS) 10.1.0 – 10.1.12), and Fixed versions are 10.0.18 and 10.1.13. |
|
What FortiGuard Coverage is available? |
• FortiGuard Intrusion Prevention System (IPS) Service: FortiGuard IPS Service is available to detect and block exploit attempts targeting CVE-2025-68645. Intrusion Prevention | FortiGuard Labs |
Welcome!Log into your account