December 2025 witnessed a dramatic 120% increase in high-impact vulnerabilities, with Recorded Future’s Insikt Group® identifying 22 vulnerabilities requiring immediate remediation, up from 10 in November. The month was dominated by widespread exploitation of Meta’s React Server Components flaw.
What security teams need to know:
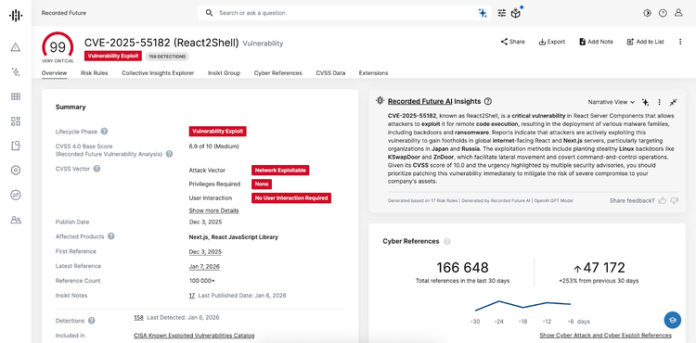
- React2Shell pandemonium: CVE-2025-55182 triggered a global exploitation wave with multiple threat actors deploying diverse malware families
- China-nexus exploitation intensifies: Earth Lamia, Jackpot Panda, and UAT-9686 leveraged critical flaws for espionage operations
- Public exploits proliferate: Eleven of 22 vulnerabilities have proof-of-concept code available, accelerating exploitation timelines
- Legacy vulnerabilities resurface: CISA added 2018-2022 era flaws to its Known Exploited Vulnerabilities (KEV) catalog, highlighting persistent patch gaps
Bottom line: December’s surge reflects both new zero-days and renewed interest in legacy vulnerabilities. React2Shell alone demonstrates how quickly modern web frameworks can become global attack vectors.
Quick Reference Table
All 22 vulnerabilities below were actively exploited in December 2025.
Score
Table 1: List of vulnerabilities that were actively exploited in December based on Recorded Future data (Source: Recorded Future)
Key Trends in December 2025
Affected Vendors
- Fortinet continued vulnerability concerns with two critical authentication bypass flaws
- Google faced three vulnerabilities across Android (2) and Chromium (1) platforms
- Microsoft dealt with a Windows kernel use-after-free vulnerability
- Meta experienced the month’s most impactful vulnerability with React2Shell
- Additional affected vendors: Array Networks, Gogs, Gladinet, ASUS, Cisco, Apple, SonicWall, WatchGuard, MongoDB, Digiever, Sierra Wireless, OSGeo, RARLAB, D-Link, and OpenPLC
Most Common Weakness Types
- CWE-22 – Path Traversal
- CWE-347 – Improper Verification of Cryptographic Signature
- CWE-416 – Use After Free
- CWE-434 – Unrestricted Upload of File with Dangerous Type
- CWE-787 – Out-of-bounds Write
Threat Actor Activity
React2Shell exploitation dominated December’s CVE activity:
- Threat actors observed to have exploited this vulnerability:
- China-nexus actors Earth Lamia and Jackpot Panda
- China-linked clusters UNC6600, UNC6586, UNC6588, UNC6603, and UNC6595
- North Korea-linked and financially motivated groups
- Observed payloads included EtherRAT, PeerBlight, CowTunnel, ZinFoq, Kaiji variants, Zndoor, RondoDox, MINOCAT, SNOWLIGHT, COMPOOD, HISONIC, ANGRYREBEL.LINUX, and Weaxor ransomware (using a Cobalt Strike stager)
- Infrastructure connections to HiddenOrbit relay infrastructure and GobRAT relay component
Additional activity:
- UAT-9686 exploited Cisco Secure Email Gateway (CVE-2025-20393), deploying AquaShell, AquaPurge, and AquaTunnel
- Unknown actors leveraged Gogs vulnerability (CVE-2025-8110) for Supershell malware deployment
Priority Alert: Active Exploitation
These vulnerabilities demand immediate attention due to confirmed widespread exploitation.
CVE-2025-55182 | Meta React Server Components (React2Shell)
Risk Score: 99 (Very Critical) | CISA KEV: Added December 5, 2025
Why this matters: Unauthenticated RCE affects React and Next.js, among the world’s most popular web frameworks. Multiple threat actors are actively exploiting vulnerable instances with diverse malware payloads.
Affected versions:
- React packages: react-server-dom-webpack, react-server-dom-parcel, react-server-dom-turbopack (19.0.0, 19.1.0, 19.1.1, and 19.2.0)
- Next.js: 15.x, 16.x, and Canary builds from 14.3.0-canary.77
- Also affects: React Router, Waku, RedwoodSDK, Parcel, Vite RSC plugin
Immediate actions:
- Upgrade React to 19.0.3, 19.1.4, or 19.2.3 immediately
- Update Next.js to 16.0.7, 15.5.7, 15.4.8, 15.3.6, 15.2.6, 15.1.9, or 15.0.5
- Monitor for unusual multipart/form-data POST requests consistent with Next.js Server Actions / RSC endpoints
- Check logs for E{“digest” error patterns indicating exploitation attempts
- Review server processes for unexpected Node.js child processes
Exposure: ~310,500 Next.js instances on Shodan (US, India, Germany, Japan, Australia)

CVE-2025-20393 | Cisco Secure Email Gateway
Risk Score: 99 (Very Critical) | Active exploitation by UAT-9686
Why this matters: Chinese threat actors are actively compromising email security infrastructure to establish persistent access and pivot into internal networks.
Affected products: Cisco Secure Email Gateway and Secure Email and Web Manager running AsyncOS
Immediate actions:
- Apply Cisco’s security updates immediately
- Monitor Spam Quarantine web interface access logs
- Check for modifications to
/data/web/euq_webui/htdocs/index.py - Hunt for AquaShell, AquaPurge, and AquaTunnel indicators
- Review outbound connections to suspicious IPs
Known C2 infrastructure: 172.233.67.176, 172.237.29.147, 38.54.56.95 (inactive)