Google Cloud Platform (GCP) Dialogflow Service Agent Token Leak and Abuse Through Conversational Agents
Tenable Research has identified and responsibly disclosed a critical privilege escalation vulnerability in Google Dialogflow. This flaw allowed an attacker with access to a Dialogflow agent to take over the Dialogflow service agent and assume its privileged permissions.
This vulnerability stems from a misconfiguration in how Dialogflow’s conversational agents handle authentication for their internal tools. When a user interacts with a predefined or custom agent, certain tools (such as the BigQuery tool) are executed using the Dialogflow service agent’s identity. This service agent is provisioned with a broad set of permissions across various Google Cloud services.
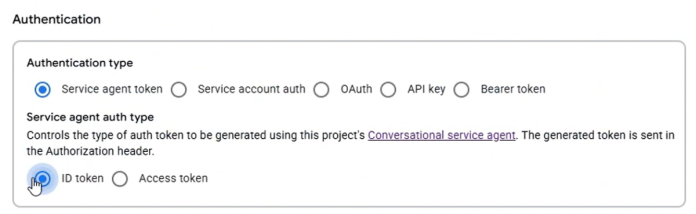
An attacker could exploit this by configuring an agent to use a tool with an ID token authentication method and a Google API URL. When the victim interacts with the agent and triggers the tool, the service agent’s ID token is used to authenticate to the API. This vulnerability allows users with the dialogflow.tools.update permission to invoke Cloud Functions and Cloud Run without explicit IAM permissions for Cloud Functions or Cloud Run invocation.
Proof of Concept
- Access Diagflow CX
- Create the predefined Movies agent
- Go to Tools –> bq tool
- Change the authentication method to ID token with a service agent
- Change the URL to an external API
- Communicate with the agent and trigger the tool
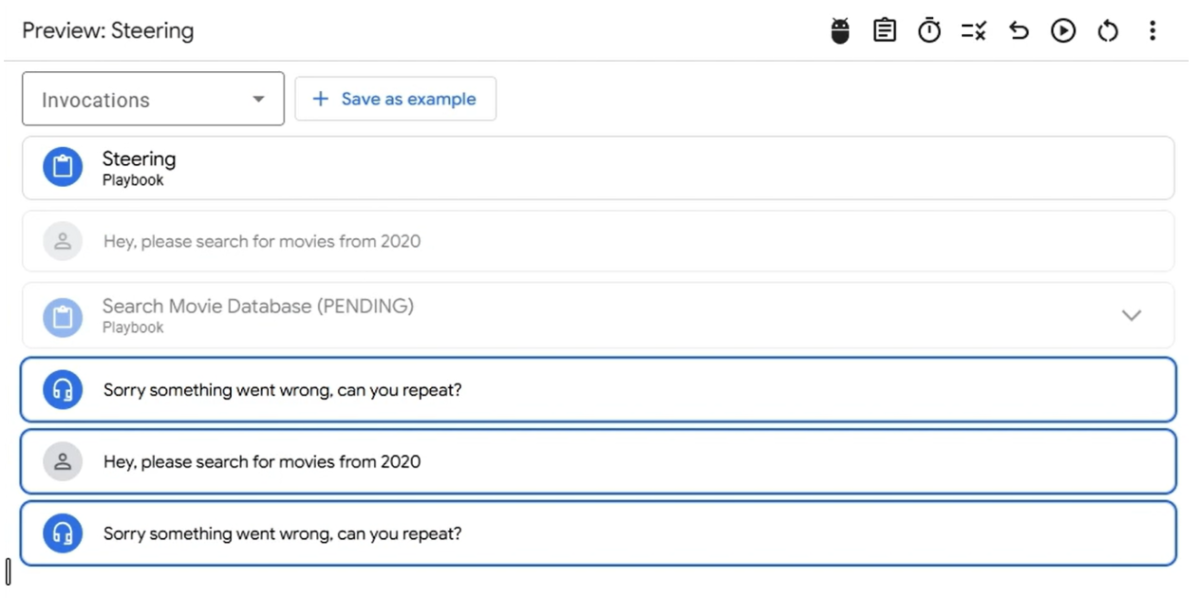
- API is called with the Service Agent permissions