Criminals, ATMs and a cup of coffee
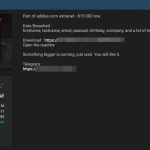
In spring 2019, we discovered a new ATM malware sample written in Java that was uploaded to a multiscanner service from Mexico and later...
ViceLeaker Operation: mobile espionage targeting Middle East
In May 2018, we discovered a campaign targeting dozens of mobile Android devices belonging to Israeli citizens. Kaspersky spyware sensors caught the signal of...
The Executive’s Guide to the CIS Controls
The Executive's Guide to the CIS Controls #outlook a{ padding:0; } body{...
Introducing Imperva Cloud Data Security!
We at Imperva are gearing up for the inaugural AWS re:Inforce event on June 25th and 26th in Boston, Massachusetts, where technical leaders will...
Centrify Closes Out a Busy June at AWS Re:Inforce and Identiverse
June has been a busy month in the cybersecurity space! It started off with InfoSec Europe and SailPoint Navigate, next week we’ll wrap up...
Not-so-dear subscribers
Many people have had a run-in with subscriptions to mobile content providers. They appear out of the blue, and get discovered only when account...
Bare Metal Provisioning
Read more
UK’s Largest Mobile Carrier Relies on AWS and Imperva FlexProtect for Web Delivery and...
In today’s highly-competitive telecommunications market, the website is integral to successful and fast customer service. Downtime due to intrusion, data breach, or DDoS attack...
Minimizing Exposure to Ransomware Attacks with Centrify Zero Trust Privilege
Ransomware attacks like the ones that wreaked havoc in Baltimore, Maryland, Albany, New York, and Genesee County, Michigan are dominating the headlines in 2019....