Infonomics-based Model Teaches CISOs how to Assess their Data’s Financial Risk, Invest Properly in...
Here’s what I consider the biggest contradiction in cybersecurity: the most-financially-damaging, reputation-destroying security incidents almost always involves the theft of millions of database records....
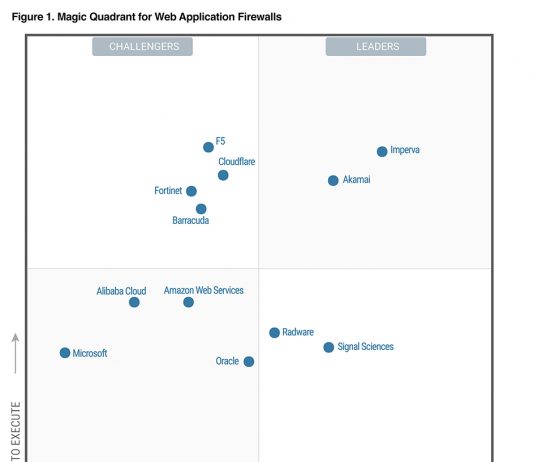
Cloud WAAPs Are the Future of Application Security. But What Does That Mean?
Millions of Verizon FIOS broadband users vulnerable to hackers controlling and surveilling their home networks.
Thousands of GPS watches whose maps were open to attackers...
Take these Five Steps to Really Mitigate your Data Breach Risks
Data breaches are a CSO/CISO’s worst nightmare. And they’re getting bigger and more damaging all the time. It’s no longer just hundreds of millions...
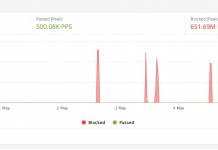
Botnet-led DDoS Attacks Are Hitting Record Intensities. Imperva is Mitigating All of Them.
DDoS attacks are usually ranked by the amount of bandwidth involved, such as the 2018 GitHub attack that peaked at 1.35 Terabits per second...
Developers Versus Automation Engineers: How We Ended the Fighting with the Right CI Process
Hey developers and DevOps professionals: what if I told you that how you wrap and execute your automation tests could be the key to...
Maintaining Privacy in the Cloud [Podcast Discussion]
Not long ago I joined Brian Contos, CISO and VP of Product Innovation at Verodin, for one of his Verodin Cybersecurity Effectiveness Podcasts.
It’s been...
Casino Goes All In and Wins Big with Imperva Security
There’s no good time to be hit by ransom-seeking DDoS attackers. For one casino-entertainment provider, the timing was particularly bad — right before one...
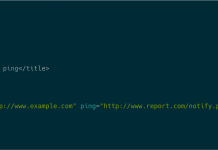
The Ping is the Thing: Popular HTML5 Feature Used to Trick Chinese Mobile Users...
DDoS attacks have always been a major threat to network infrastructure and web applications.
Attackers are always creating new ways to exploit legitimate services...
Making Our Security Portfolio Simpler — and Better
Since its inception in 2009, Incapsula has been a proud part of Imperva, the analyst-recognized cybersecurity leader.
However, cybersecurity needs are evolving, and so...
Not just for Processing: How Kafka Streams as a Distributed Database Boosted our Reliability...
The Apache Kafka Streams library is used by enterprises around the world to perform distributed stream processing on top of Apache Kafka. One aspect...